Products
From Previous Page
TEALDOC 4.51D - updated September 25, 2001
(http://www.tealpoint.com/softdoc.htm)
Powerful reader for Palm documents, e-books, and newspapers, supporting advanced features such as pictures, links, and flash cards.
TEALECHO 2.41 - updated October 4, 2001
(http://www.tealpoint.com/softecho.htm)
Digital "ink" lets you see what you write, vastly increasing graffiti writing speed and accuracy. No more writing blind!
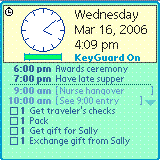
TEALGLANCE 3.35B - updated April 13, 2001
(http://www.tealpoint.com/softglnc.htm)
Pop-up utility show time, date, appointments and to-dos, and other useful information at powerup. See your day at a glance.
TEALINFO 3.11B - updated December 26, 2000
(http://www.tealpoint.com/softinfo.htm)
A system for creating and browsing interactive databases, reference works, and mini-application folios; a handheld reference library.
TEALLAUNCH 2.60B - updated October 1, 2001
(http://www.tealpoint.com/softlnch.htm)
A pop-up application launcher and mapping utility for launching apps and special functions from pen taps, graffiti strokes, or button presses.
TEALLOCK 3.70B - updated July 26, 2001
(http://www.tealpoint.com/softlock.htm)
Secure automatic locking program with optional data encryption and numerous activation and customization options.
TEALMAGNIFY 2.10 - updated Sept 13, 2000
(http://www.tealpoint.com/softlens.htm)
An ever-ready magnifying glass that works with most any program, TealMagnify saves your eyes when looking at tiny text.
TEALMASTER 1.44 - updated June 11, 2001
(http://www.tealpoint.com/softmstr.htm)
A supercharged Hackmaster replacement with 100%-compatibility and enhanced stability, configuration, diagnostic and activation features.
>> Continued...
|
|
Hacks on your Handheld
Continued from Previous Page
Hacks work by replacing one or more system routines with
their own code. Any apps trying to use a replaced system
routine end up using the hack's code instead. The hack
gets the parameters the original routine would have
gotten. It also gets the location of the original
routine, so it can run that routine if it needs to
(called "passing-through"), sometimes after first
modifying the parameters. For instance, one could write
a relatively useless hack to reverse text drawn to the
screen by replacing the WinDrawChars routine. In the
previous example, the hack would get the parameters (
"Hello", 5, 0, 0 ), but would reverse the text in the
first parameter to ( "olleH", 5, 0, 0 ) before calling
the original system routine to do the actual drawing.
Types of Hacks
Hacks replace system functions for different reasons.
They can be categorized into three basic categories.
'Replacement' Hacks
"Replacement" hacks duplicate a system routine's
functionality entirely, and do not pass-through to the
original routine. FindHack is one example. When one
taps on the silkscreened "find" button, FindHack, if
active, brings up its own window to let the user perform
an enhanced search operation. It does not call the
system routine afterwards, as doing so would also bring
up the original system window asking to perform the same
search that was just completed.
'Enhancement' Hacks
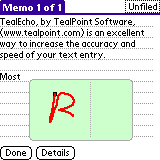 Unlike replacement hacks, "enhancement" hacks do call the
original system routine. When doing so, they either
modify the passed parameters before passing them on, or
use them to perform a related function. TealEcho is an
enhancement hack. It hooks into a system routine used to
save pen strokes for the graffiti system. TealEcho still
passes through the pen strokes to the original routine,
but also uses this information to draw the strokes onto
the screen as you write.
Unlike replacement hacks, "enhancement" hacks do call the
original system routine. When doing so, they either
modify the passed parameters before passing them on, or
use them to perform a related function. TealEcho is an
enhancement hack. It hooks into a system routine used to
save pen strokes for the graffiti system. TealEcho still
passes through the pen strokes to the original routine,
but also uses this information to draw the strokes onto
the screen as you write.
'Parasitic' Hacks
Parasitic hacks are perhaps the most common. They
resemble enhancement hacks, but function in ways not
directly related to the routines they hook into.
Instead, they use the system routines simply as a way to
trigger their activation. Pop-up programs like printHack
and TealLaunch fit into this category. Most of these
hacks hook into the system routines "SysHandleEvent" or
"EvtGetEvent". These are two routines that programs
regularly call in response to screen taps, button
presses, and other system messages. Parasitic programs
tend to hook into one or the other, passing through to
the original routines. They watch for one or more
specific pen strokes or button presses, and activate only
when a certain combination is seen.
>> Continued on Next Page...
News Home
| Page 01
| Page 02
| Page 03
| Page 04
|
|